The impact and opportunities of the Telecoms Security Requirements (TSR)
Entering a new era of communications security
Following the introduction of the Telecommunications (Security) Act in November 2021, telecommunications providers large and small must now comply with ‘one of the toughest telecoms security regimes in the world’ or risk financial penalties up to £10m.
The UK government has marked out ambitious targets to connect 15 million premises to full fibre by 2025, with nationwide connection expected to be delivered by 2033. While much of the population is to be covered by 5G networks by 2027.1 Bringing far more than just increased speed, 5G will soon be central to daily life in the UK – from connective vehicles to smart factory production lines.
Yet, as the advancement in network technology accelerates and becomes further embedded in our daily lives, the threats posed from nation states and cyber criminals continue to grow. Research by Skybox Security reported a 106% increase in malware and a record-breaking 18,341 new vulnerabilities in 2020.2 Despite this, findings from the 2019 UK Telecoms Supply Chain Review Report carried out by the Department for Digital, Culture, Media & Sport (DCMS) revealed that there was little to incentivise communications providers to manage cyber security risks.
Additionally, the lack of diversity across the UK telecoms supply chain raises the possibility of critical national infrastructure balancing on single suppliers, posing a range of risks to the security and resilience of UK telecommunications networks.
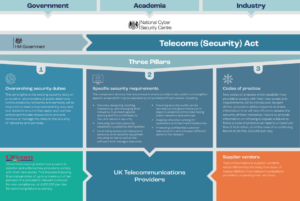
Introduced into UK law in November 2021, the UK Telecommunications (Security) Act aims to tackle the risks highlighted in the Telecoms Supply Chain Review Report by raising the bar on telecommunications network security. A core element of The Act is the establishment of a new regulatory framework for telecommunications security. The framework comprises three key components:
1. New Telecoms Security Requirements (TSR)
At the heart of the framework, the TSR marks a significant shift away from The National Cyber Security Centre (NCSC)’s now closed telecoms assurance standard model known as CAS(T). Overseen by Ofcom and Government, the new requirements will provide clarity on how providers will be expected to design and manage their networks to ensure they’re meeting the new higher bar of network security standards.
2. Establishing an enhanced legislative framework
In addition to statutory compliance of the TSR, the Act strengthens Ofcom powers to enable monitoring and assessment of operators’ security. This is to include technical testing, interviewing staff, and entering providers’ premises to view equipment and documentation. Failure to meet the new legal duties could leave providers facing hefty fines of up to ten per cent of turnover, or £100,000 per day if directives continue to be contravened.
3. Managing the security risks posed by suppliers
Telecommunications providers will need to ensure that they are managing the security risks posed by all suppliers. This will be addressed by:
- Providers having vigorous oversight of vendors to ensure they follow the TSRs
- Working closely with vendors on assurance testing of equipment, systems, and software
- New powers for the government to impose controls on telecommunications providers’ use of goods, services or facilities supplied by ‘high risk’ vendors.
Security-first is the new mantra across the industry as minimising risks to critical national infrastructure will soon become part of day-to-day operations. Bringing together legal, technical and industry perspectives, this report explores the opportunities and obstacles ahead, and how to chart your course for success in the new security era.
Telecoms (Security) Act: Three Pillars
Key considerations for communications leaders
Clear visibility is critical
Protecting your network, applications and data has never been more critical. However, blind spots, missing data, and the risk of dropped packets make management and protection of these challenging, not to mention the scale and complexity of many providers’ hybrid network infrastructure. Nonetheless, providers must ensure they are able to monitor security across the entirety of their network and can act quickly when issues arise.
Security and service quality will need to be carefully balanced
Whilst enhancing security is the ultimate goal of The Act, this cannot be at the cost of network performance. Outages themselves can put providers in breach of the regulations. Security scans are a key line of defence for network security, helping to identify vulnerabilities which can be exploited if the correct mitigation steps aren’t followed, so ensuring you have a robust vulnerability management process is critical. Incorporating the right vulnerability scanning tools and following the required change management processes to correctly implement tools will help to secure your network whilst minimising any potential performance impact to your existing infrastructure or service outages.
Auditing abilities are a new superpower
Demonstrating compliance with the new legislation may pose a significant challenge to providers, particularly as they attempt to flow down security standards and audit requirements into the supply chain. However, implementation of robust auditing processes to identify and eliminate weaknesses and vulnerabilities are a must for keeping providers on the right side of the regulations.

Knowledge is power
With any significant legislature change comes a period of uncertainty as businesses adapt to change, so getting to grips with the new regulation changes ahead of the game is key. Many providers have already begun the search for talent with the technical skills and experience to deliver their TSR programmes; however, with the jobs market at boiling point, some providers may find utilising external partnerships provides a more practical route to successful delivery as well as a means to upskill and educate internal teams.
You’ll be tested
In 2019, OFCOM took over TBEST – the intelligence-led penetration testing scheme – from DCMS and has been working with select providers on implementation of the scheme. Whether through TBEST or not, providers will be expected to carry out tests that are as close to ‘real life’ attacks as possible.
The difficulty will be in satisfying the requirement:
“that the manner in which the tests are to be carried out is not made known to the persons involved in identifying and responding to security compromises.”
Providers may need to work with an independent vendor to ensure compliant testing.
Costs are still unclear
While the costs for complying with the new regulations are still undermined, an earlier impact assessment of the proposed legislation carried out by the government indicated that initial costs are likely to be hefty:
“Feedback from bilateral discussions with Tier 1 operators have indicated that the costs of implementing the NCSC TSR would be significant. The scale of these costs is likely to differ by size of operator and could be of the scale of over £10 million in one off costs.”
Culture may challenge change
Technology will, of course, be at the forefront of communications leaders’ minds, yet the cultural changes required to successfully embed a security-first mindset are of equal importance and must be considered in equal measure. Change is never easy, particularly when there is a fixed deadline in place; however, delivery that is well designed and meticulously planned is key. Ultimately, the onus will be on leaders to craft a clear vision – achieving network security that is intrinsic by design – as well as mapping out the road to get there.
Roadmap to Compliance: How to prepare for the regulatory road ahead

Identify your gaps
Understanding your current state is the first step in achieving a successful transformation. A full audit of your security strategies, plans, policies, and effectiveness will expose your weaknesses and gaps, enabling you to take the right actions to protect your business and ensure compliance.
Prioritise your most pressing threats
While gathering data can provide better visibility of your network, taking reactive action to lower your risk isn’t the most efficient approach. Establishing levels of prioritisation will ensure your resources are being used to reduce risk in the right areas.
Get the right people in place
From gap analysis to operating model design, programme delivery, and reshoring, it’s likely you’ll need more people in place and new competencies developed. Getting the right partnerships and people now is key to getting ahead.
Plan to avoid legacy issues
Today’s telecommunications industry is built on multi-generational networks and legacy systems continue to underpin critical infrastructure. While extracting these systems is not going to happen overnight, dealing with your legacy should be an integral part of planning
Implement transparent designs
Failing to disclose evidence of a breach could result in a £10m fine, so built in transparency and traceability are key to your programme. Consider the likely information requests that are to come to ensure your design changes enable clear tracking and reporting.
Embed a security-first focus
Mitigating the risks facing the UK’s critical national infrastructure is the driving force behind the TSRs, and telecommunications providers will need to ensure that this mindset is embedded in the everyday. Buy-in from the business is core to any cultural shift, so align your leadership with a shared, cross-functional vision and get some early delivery going to build gradual momentum.
Prepare for future cybersecurity legislation
In November 2021, the Government announced The Product Security and Telecommunications Infrastructure Bill (the PSTI) to ensure consumers’ connected and connectable devices comply with tougher cybersecurity standards. As cybersecurity evolves, so too will the threats to organisations, and telecommunications providers must be prepared for more regulatory oversight.
Embrace the benefits of built-in security
Ultimately, security that is built in rather than bolted on will enable providers to offer better protection and performance for customers, as well as foster trust with greater transparency. While the industry may not have been seeking the Telecoms Security Act, its passing prompts action to remove the constraints of old and reimagine and reshape to seize the opportunities of a new era.
Start your security transformation now: How CACI can help
The Telecoms Security Act is clear – security is everyone’s priority, from executive to employee. However, embedding a security conscious culture from top to bottom requires significant resource and expertise to steer towards success. With the clock already counting down, telecommunications providers are under pressure to begin their TSR compliance journey whilst ensuring that existing change programmes stay on track.
In today’s global market where demand for security resource and competence is fierce and available talent is few and far between, companies may struggle to find the in-house resources and expertise required to meet the new regulations. With over 20 years’ experience in telecommunications, CACI can guide you through the challenges and change brought by the TSR. From auditing your current security and addressing shortfalls to full Telecoms Security Framework implementation guidance and upskilling of your internal resource, our highly experienced security and compliance experts can help prepare your organisation for the new security era.
Contact us
If you’re looking for help with your security needs and TSR compliance, please contact our expert team today.
